Case Study 1: Chain of Security
Dubbed the 4th industrial revolution, the ‘Internet of Things’ will consist of a vast network of sensor nodes that will generate an unprecedented flow of global data. These devices will quietly execute smart contracts with physical actuators that will manage many aspects of our future lives. But how secure and trustworthy is the data that we will come to rely on so heavily?
IoT 2.0+
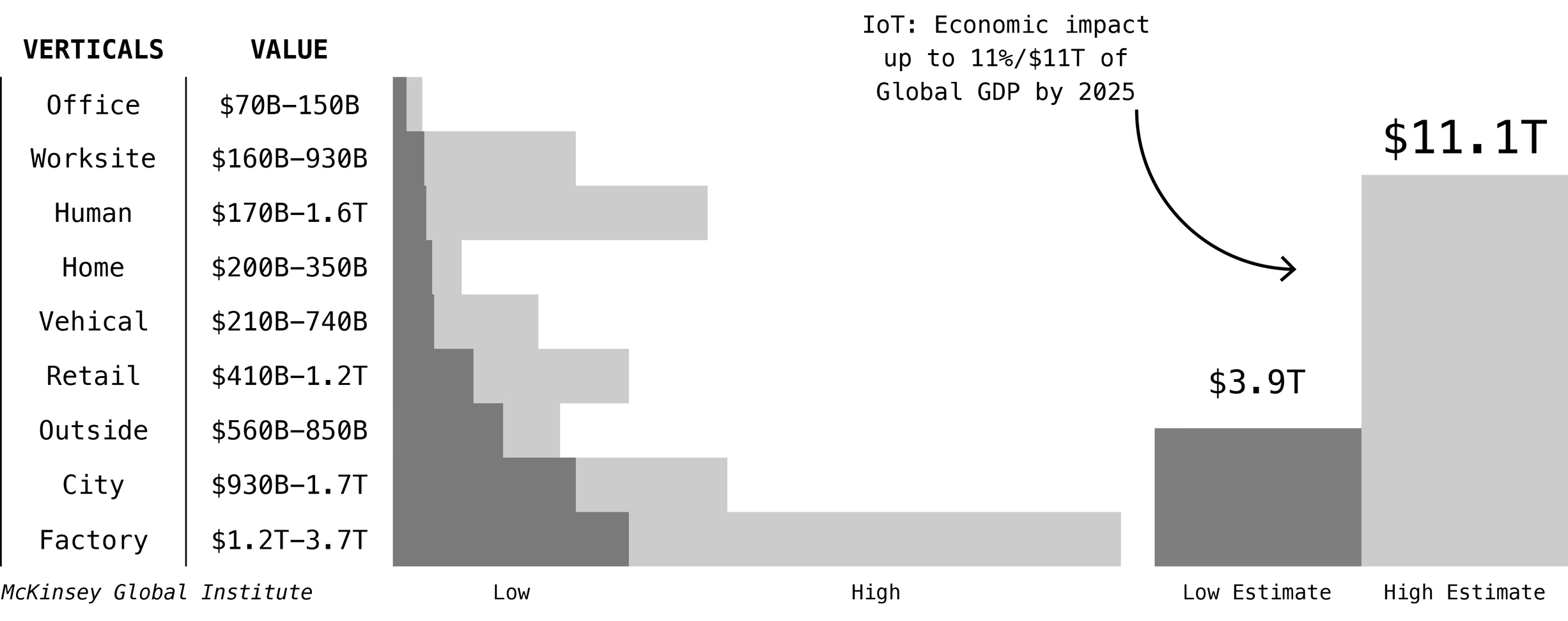
While consumer IoT garners much of the spotlight, the world of Fitbits and connected coffee machines will only make up about 22% of IoT's full potential. Our initial focus is on the impact possible through industrial IoT applications. Though we are just at the beginning, estimates from McKinsey place the potential economic impact of IoT at 4-11% of global GDP by 2025 ($3.9 trillion on the low end and $11 trillion on the high end). The economic impact from IoT is largely due to the transparency and visibility it provides to the inner workings of most all industrial systems, resulting in the identification and correction of gaps in efficiency.
One significant caveat is the fact that roughly 40% of this economic value is unobtainable without full interoperability between IoT systems - a key potential asset of blockchain. Interoperability can be achieved by implementing protocols or platforms that allow different IoT systems to ‘trust’ & communicate with one another - the direct security benefits of this cannot be overstated. Adopting open standards vs following the predictable model of proprietary sandboxed development is the best way to accomplish interoperability. This also allows public stress testing of open protocols to explore and remove all potential weaknesses.
Explosion of mystery devices
IoT suffers from potential systemic failures as it scales with disastrous consequences. Without an openly stress tested baseline protocol standard for trusted IoT interaction, fundamental security risks will become exponentially worse as 50-200 billion cheap connected devices come online by 2020. Conventional wisdom also suggests a standards war will break the industry into a series of proprietary protocol sandboxes, slowing development and pricing out many startups entering the sector.
It is our responsibility and legal imperative to explore the development of a future resistant open protocol to protect business, government and consumer data. It is negligent to grow this industry without serious consideration of the primary risk. Security should be openly available to as many as possible.
Specific problems with IoT
- Secure device connectivity
- Corruptible/spoofable individual device identity and reputation
- Possibility to watch or steal information from devices
- Hacking into devices and spoofing output data (Stuxnet)
- Physical tampering and malware manipulation
- Corruption resistant sensor impression history - need for a tamper-resistant distributed 'digital alibi'
- Danger of hub device collecting information from connected devices being hacked
- How does an actuating device prove the instructions it is receives are valid?
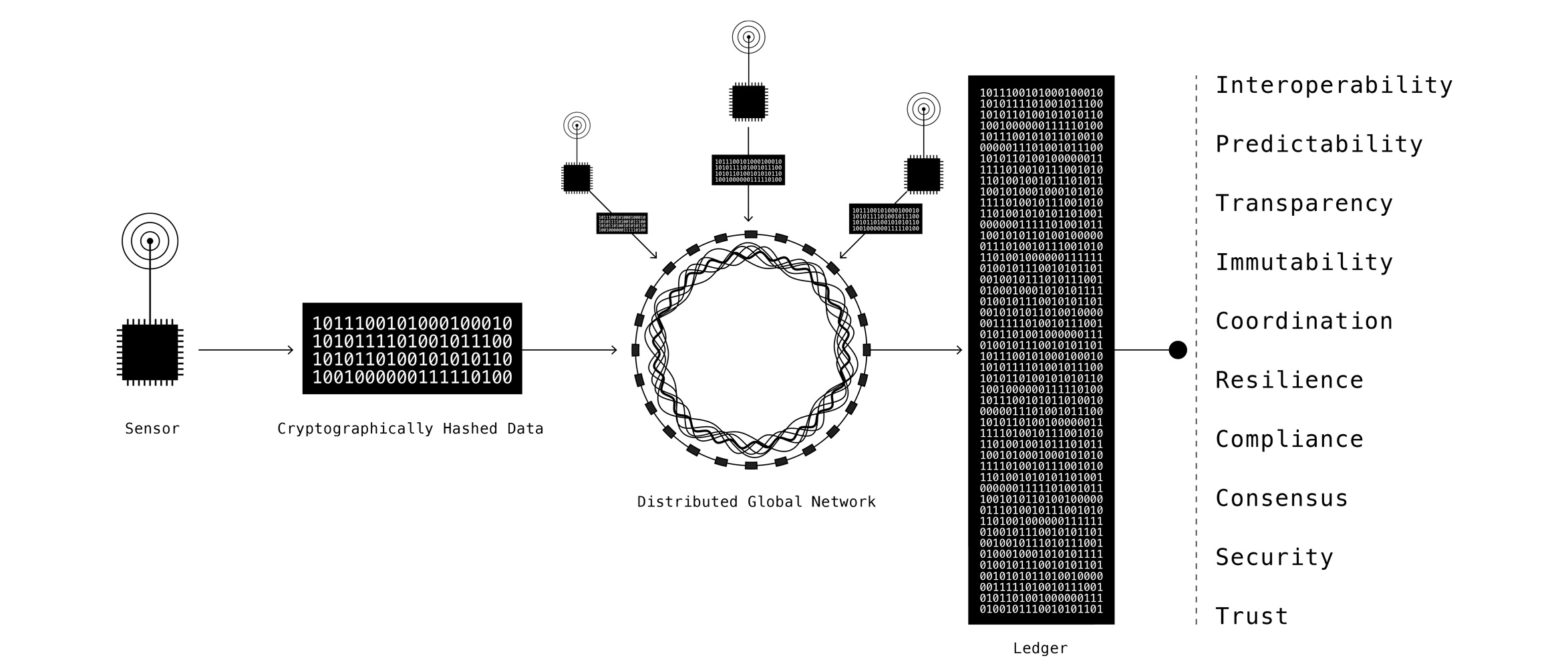
How the blockchain may help
With what is effectively a $10+ billion bug bounty, blockchain has protected the value contained within bitcoin without a single hack. While private institutions that protect bitcoin have been been hacked, the baseline currency has not been successfully manipulated on a significant scale. Due to this particularly odd show of durability, it is worth investigating further if blockchain has a role to play in securing IoT.
Applications of blockchain technology in context of IoT security
Device Firmware Hashing
Device firmware can be hashed into a Blockchain on a continual basis. If the firmware state changes (by even a single digit) due to malware altering the firmware code, can the hash failure will alert the device owners to foul play. This is not dissimilar to an immune system flagging a foreign body.
Instruction Authentication
Information or checking instructions - device hashes information it wants to send to another device and places the hash into a Blockchain...the receiver of the information hashes the same information...if the hash matches the hash on the Blockchain then the information has not changed in transit.
Device Identity Protocol
Device Identity Protocol. Each device has a Blockchain public key. Devices encrypt messages to each other (challenge/responses) to ensure the device is in control of its own identity. Is it best to require a universal identity protocol for all devices?
Device Reputation Systems
Devices develop reputations in the same of Keybase.io - each device has a public key. Cryptographic reputation systems are overlaid over devices. There could be, for instance, a certification agency for devices which audits the device and then gives it an identity on the Blockchain. So once the device is historically 'born on the Blockchain' the device’s identity will be irreversible. Can the environmental inputs that are unique to an individual sensor, such as GPS, temperature/humidity, etc., be used in conjunction with IMEI & OEM firmware hashes create the ultimate in tamper-resistant unique device identification?
Managing IOT data
With the enormous amount of IoT sensor data vs. traditional financial transaction data, how will orthodox Blockchain formats adapt to handle the scale of IoT? If data needs to be siloed traditionally, how will this system handle security of accessing those silos?
Controlling IoT updates
"I don’t want my IoT devices to automatically update if the update has not been voted by a community of experts. This doesn’t guarantee that there won’t be any backdoors (intentional or not) but it sure makes it harder. The idea is that when an update is pushed to a distributed consensus platform, it needs a minimum number of signatures from a pool of recognised experts before the IoT devices apply it. Think of a multi-sig (P2SH) transaction in Bitcoin.
The other benefit of blockchain tech is the immutable history of updates. It just fits nicely."
"I can see a scenario where a pool of pre-arranged signers (say a committee of well-known security experts) wants to vote (or not) on the security merits of a particular software release but wishes to remain anonymous within that group. Ring signatures provide that anonymity within the group. I can see pros and cons of anonymous voting, but the fact that it’s an available option is good." - Filipe Farinha
Code on a publicly available database
Assuming the public blockchain is visible and that the device’s ‘constitution’ (aka smart contract) is in a piece of code on the public blockchain then the device can only do what the code says. The code (according to Fabian Vogelsteller) is “(potentially) unchangeable and verifiable”. It is presumably unchangeable due to the code ‘coming to life’ in a transaction on the blockchain and, the assumption here, is that no human intervention is required thereafter to maintain the device’s ‘constitution’. The code is ‘verifiable’ due to you being able to read it on the public database. The key point is that there is no need to trust how the device will behave if its ‘constitution’ is publicly available.
Collaborate
Contact us below if you are interested in exploring blockchain's potential to add security and interoperability to the Internet of Things.